LDAP User Administration
The LDAP integration allows users to authenticate to AGNES Connect using an existing LDAP server, allowing users to take advantage of existing single sign on solutions. The LDAP server must be publicly available on the internet to communicate with AGNES Connect servers. Each organization may connect to a single LDAP server, replacing the user management module provided by AGNES Connect. These settings are typically configured by AMD employees during the initial deployment. Changing these settings may interfere with an organization’s ability to connect to AGNES. It’s recommended making changes to these settings under the guidance of AMD.
Configuration Suggestions
The responsibility for LDAP user management lies with the organization’s IT group. However, AMD recommends incorporating an administrative group called agnes_admin. When configured as the administrative group in AGNES, members of this group will gain administrative privileges in AGNES Connect. The service user will provide baseline access to the server as the Bind DN.
Navigate to Organization Settings
Open Site Manager
To edit this setting, the logged-in user account must have an administrator role.
Right-click the AGNES Connect icon in the system tray and select Site Manager.
Select Organization from the navigation bar
Click the ’≡’ icon in the top left of the home screen, and select Organization from the navigation bar. If the option is not available, ensure the logged in user account has the administrator role.
Select LDAP User Administration Settings
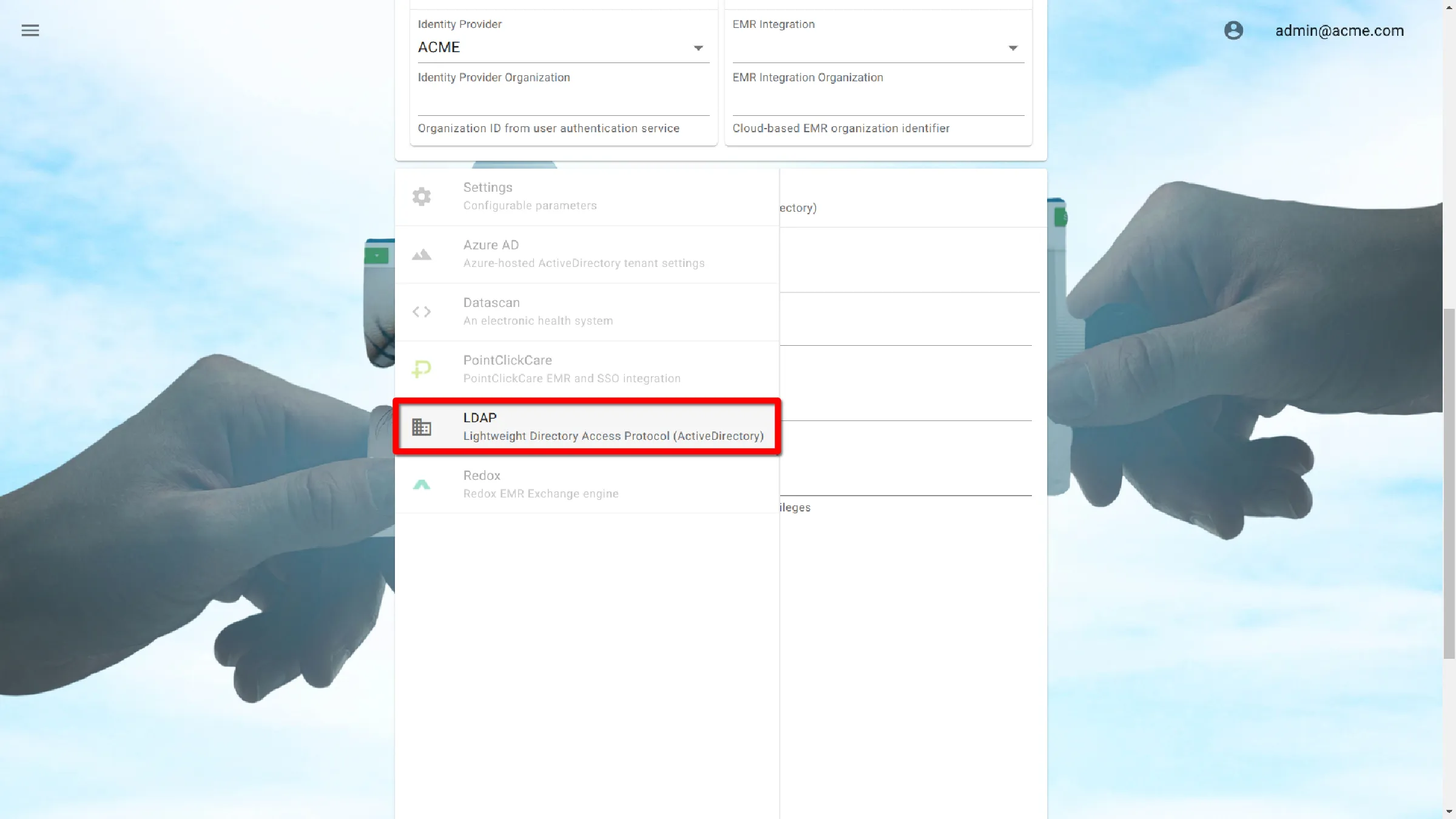
LDAP Settings
All LDAP credentials entered in to AGNES are listed in the organization’s LDAP management portal. That portal is managed by the organization and not available to AMD.
Select Base Settings
URL
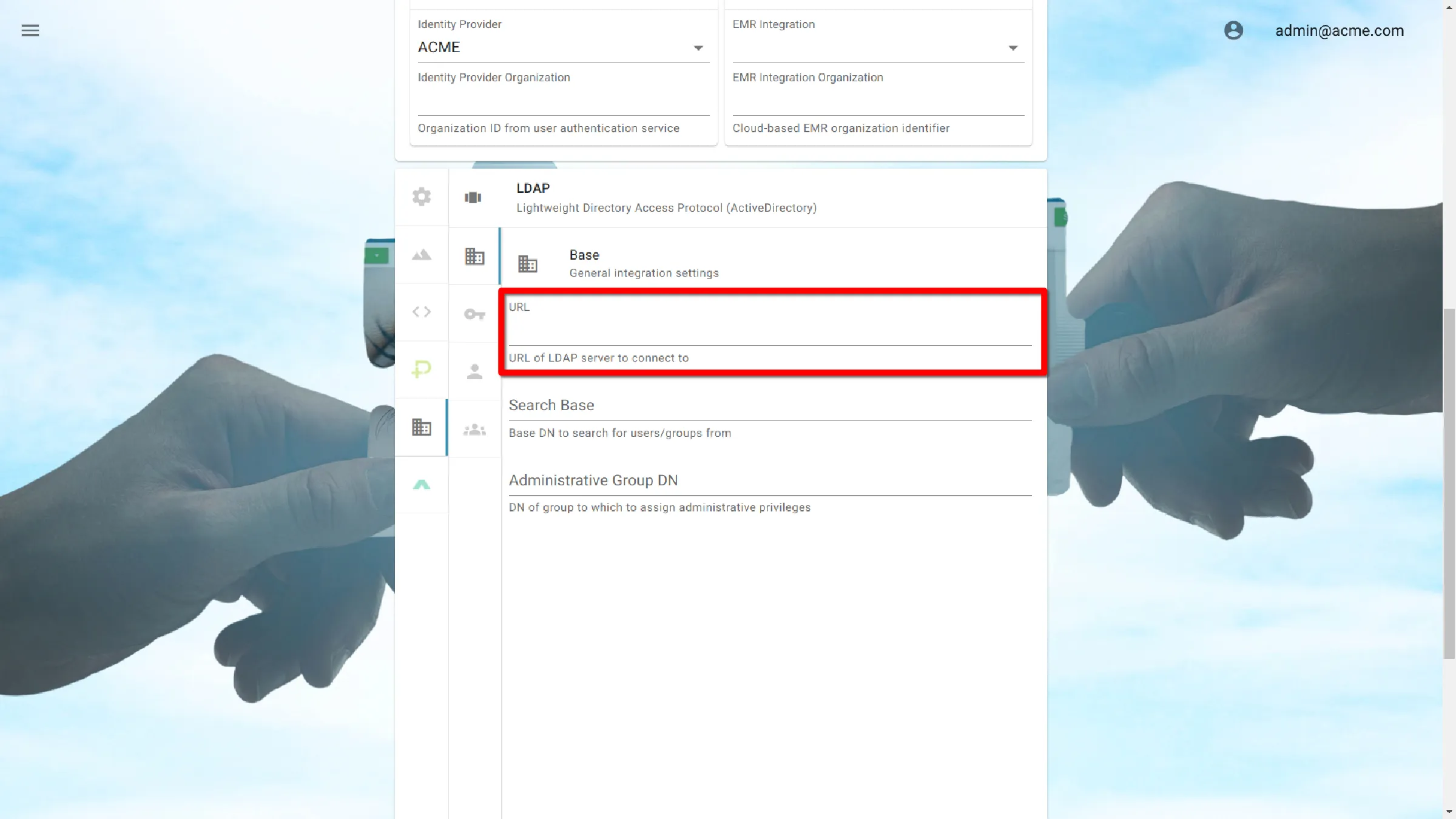
Enter the public IP and port of the LDAP server. It should be prefixed with ldap://
To connect to a server with the IP of 1.2.3.4, using the default port 389, the input would be:
ldap://1.2.3.4:389
Search Base
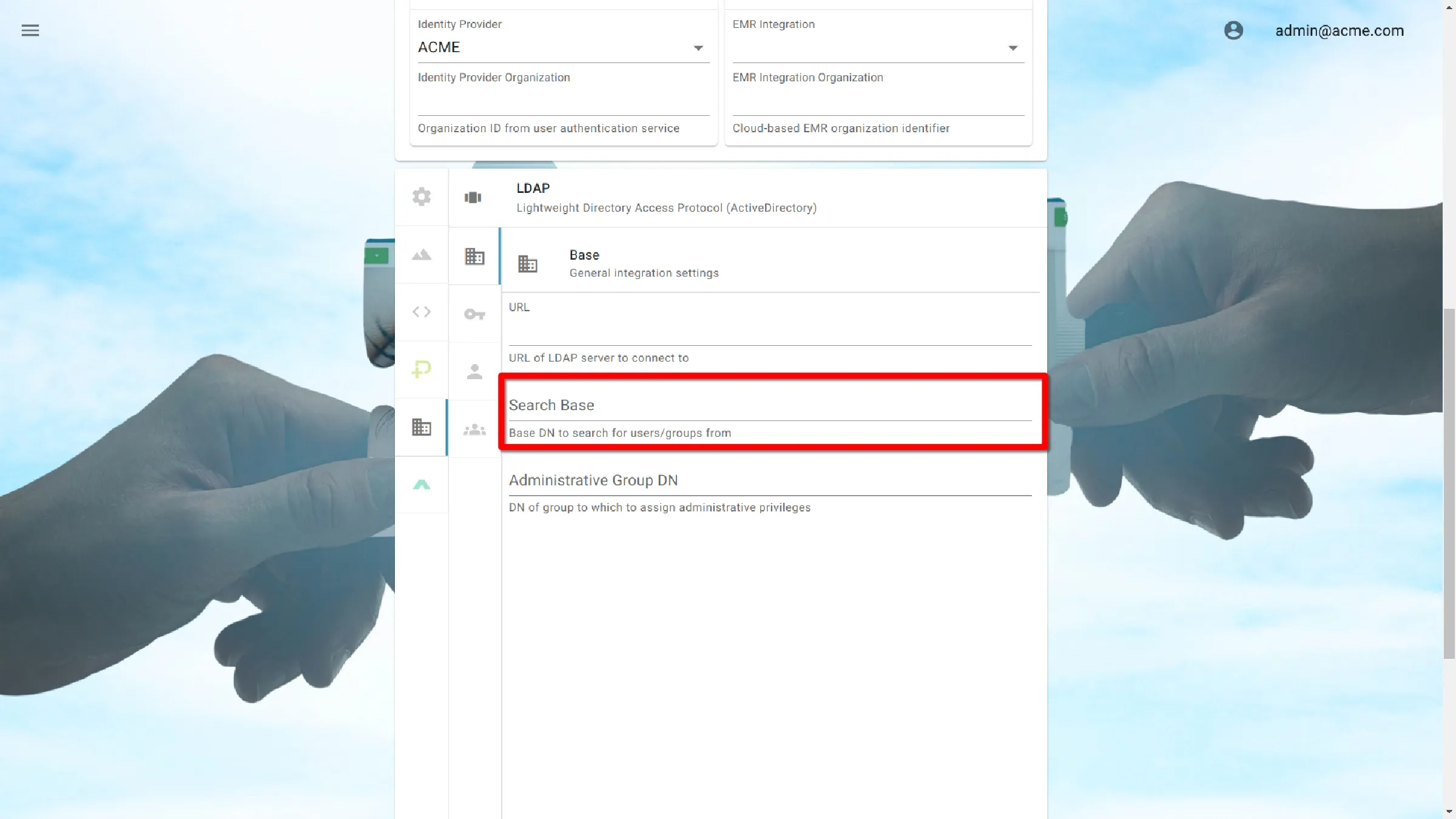
Search Base indicates the starting point for a search in the LDAP directory. To allow full querying, specify the root of the directory service. Alternatively, refine access controls by specifying an organizational unit (OU).
Search Base comprises multiple objects separated by commas. These objects include:
- cn common name
- ou organizational unit
- o organization
- c country
- dc domain
To allow all users in the mycompany.dom domain, specify:
dc=mycompany,dc=dom
Narrow the search by specifying an organizational unit.
ou=support,dc=mycompany,dc=domain
Administrative Group DN
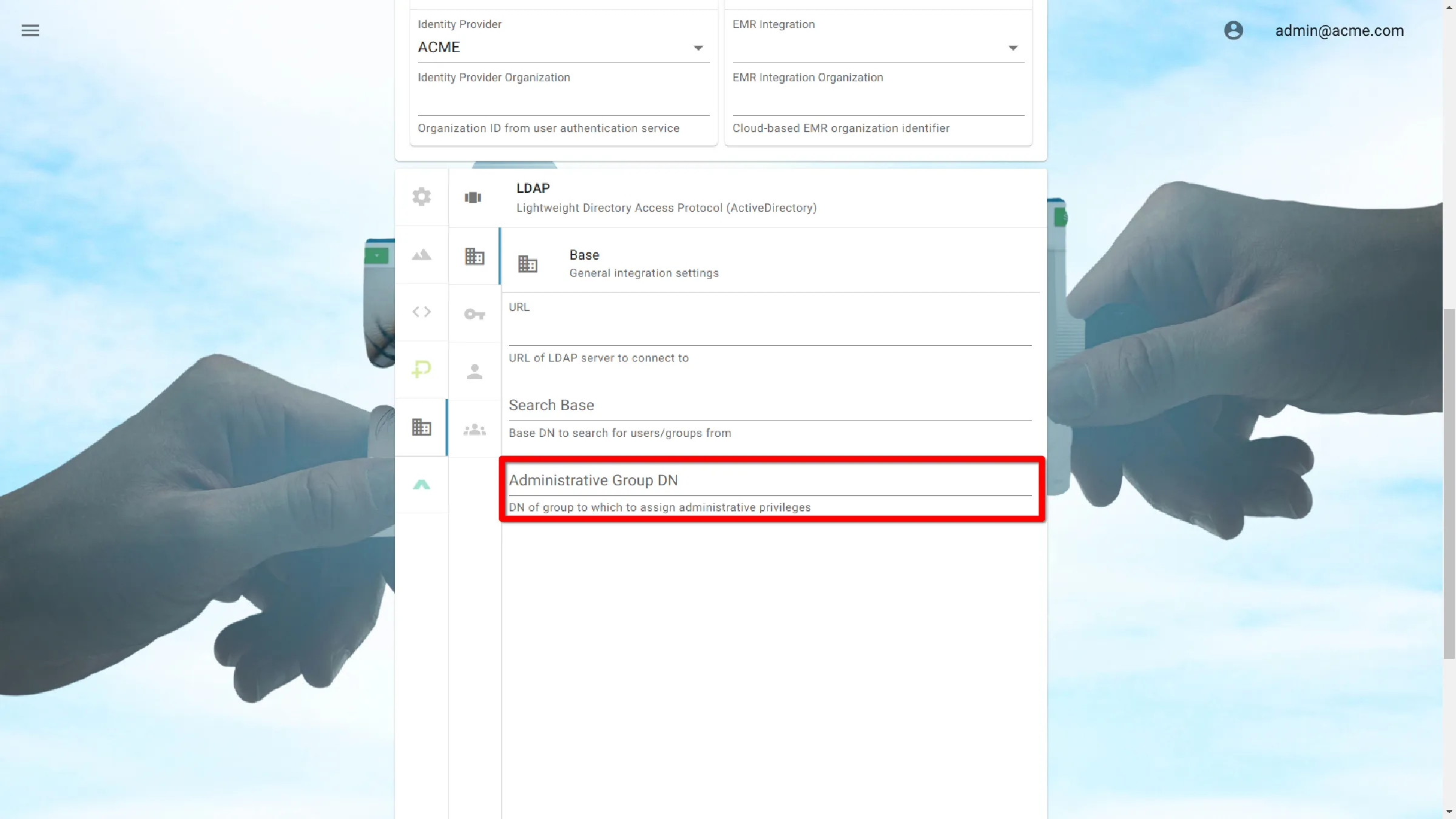
This entry controls who is allowed to administer AGNES Connect within the organization by allowing the specification of a User or Group DN.
A Distinguished Name (DN) uniquely identifies an entry and describes its position in the Directory Information Tree (DIT).
DN’s consist of components separated by commas called Relative Distinguished Names (RDN). These include:
- uid user id
- ou organizational unit
- dc domain
To allow members of the group agnes_administers to administer General, specify:
ou=agnes_administers,dc=mycompany,dc=domain
To allow just the user john.doe to administer AGNES, specify:
uid=john.doe,ou=agnes_administers,dc=mycompany,dc=domain
Bindings
Bindings are required to gain permission to the LDAP server to authenticate users. They consist of two parts, Bind DN and Bind Password.
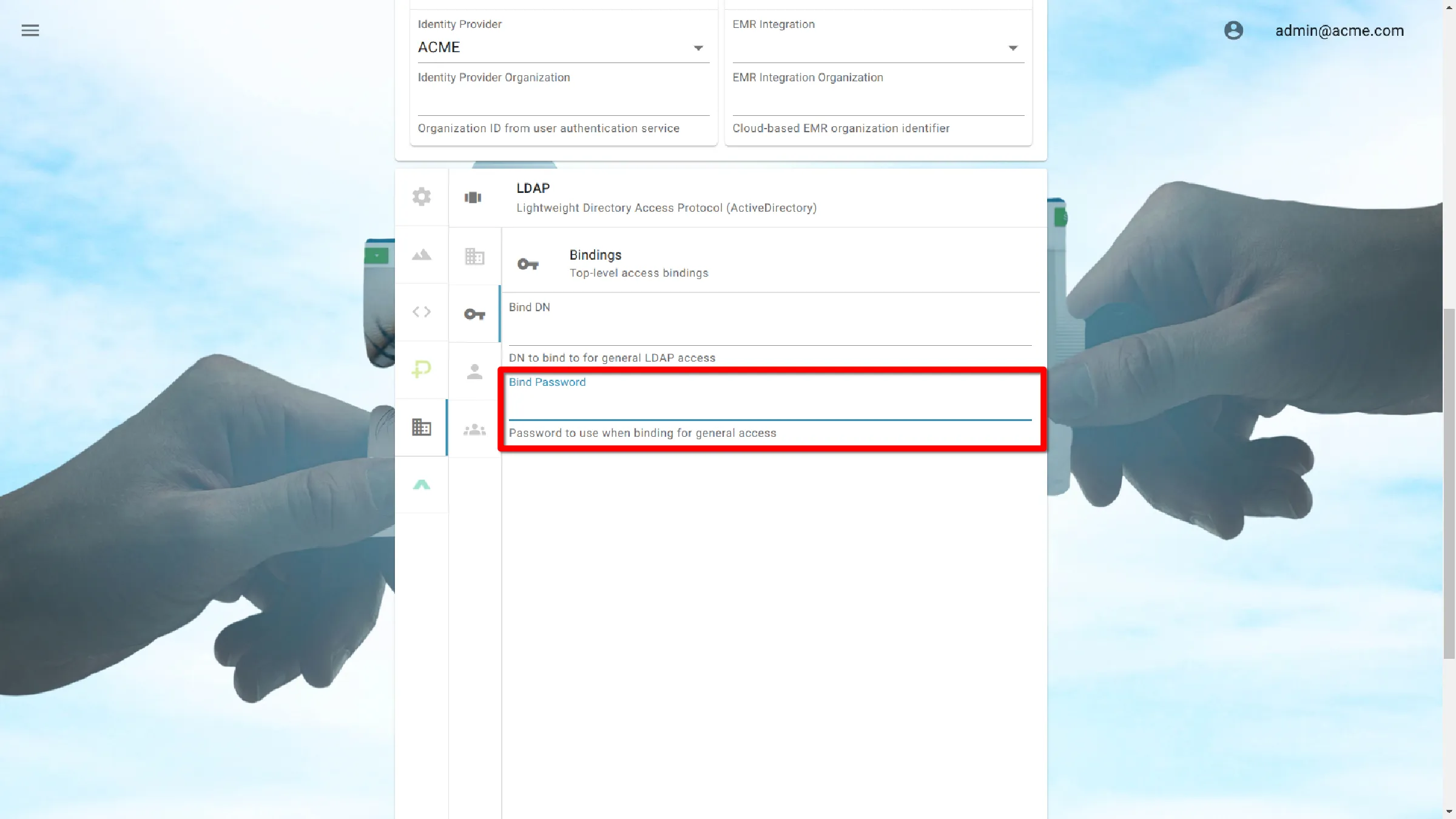
Bind DN

Bind DN is the Distinguished Name that provides permission for AGNES to authenticate users against the LDAP server.
Bind DNs consist of components separated by commas. These include:
- cn common name
- ou organizational unit
- dc domain
An example Bind DN would look like:
cn=agnes_ldap,ou=agnes_administers,dc=mycompany,dc=domain
Bind Password
Bind Password is the password associated with the Bind DN account.
User Settings
User Settings define which identifiable attributes will be looked for when querying the Directory Information Tree (DIT).
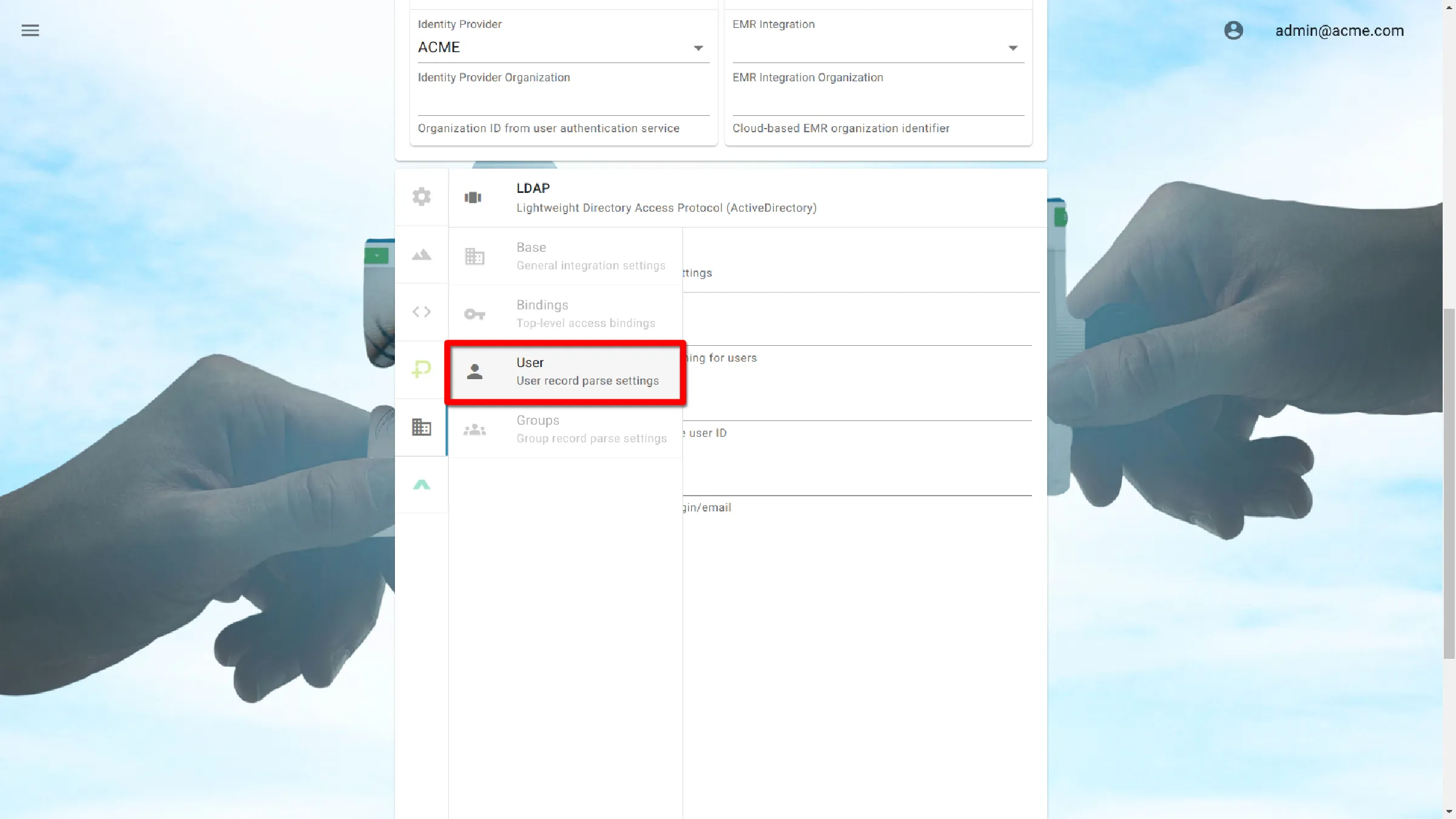
Object Class
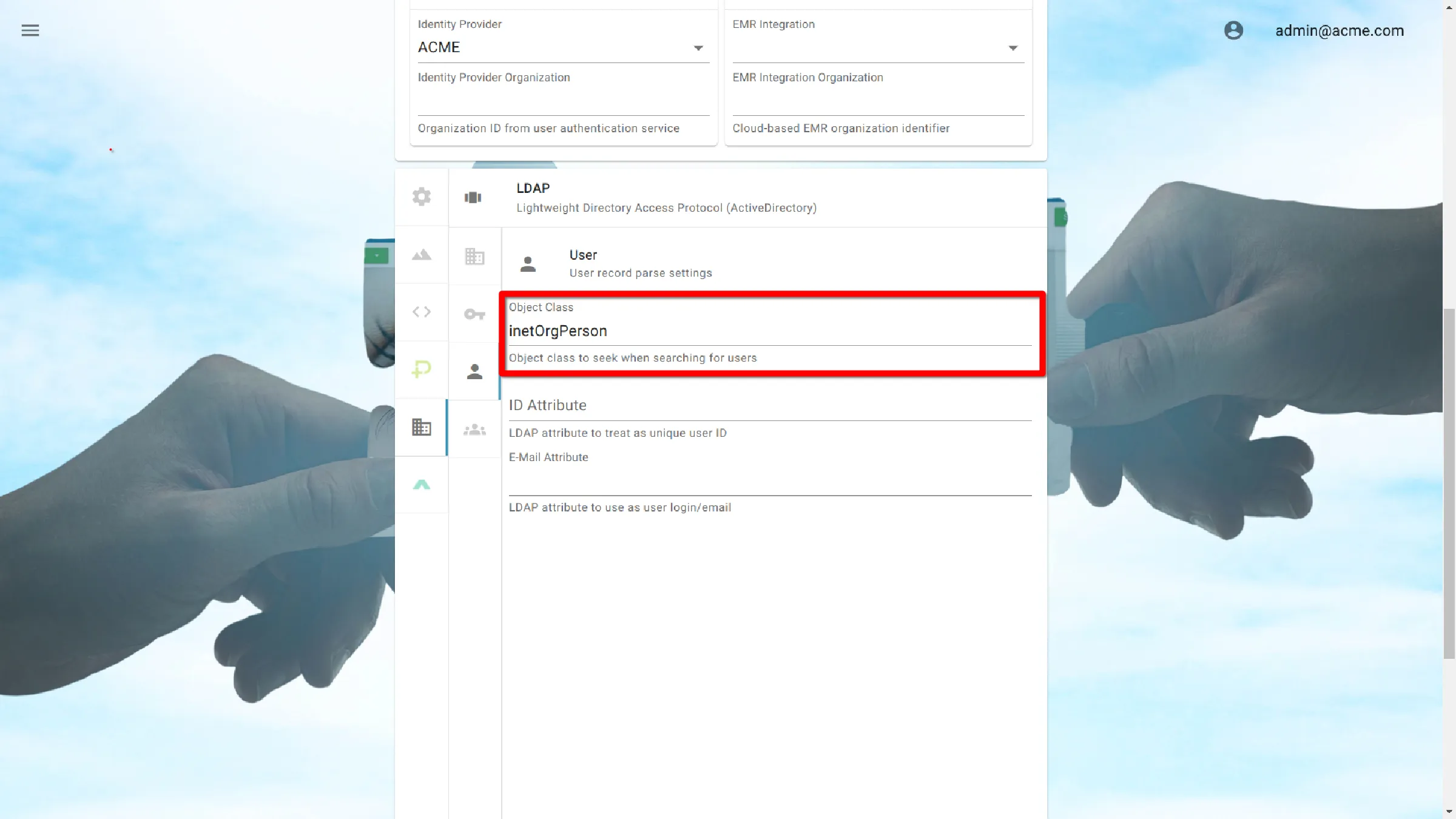
The Object Class attribute is used to help determine the permitted attributes of an entry.
This represents the type of object that will be classified as a user.
Active Directory
organizationalPerson
LDAP
InetOrgPerson
ID Attribute
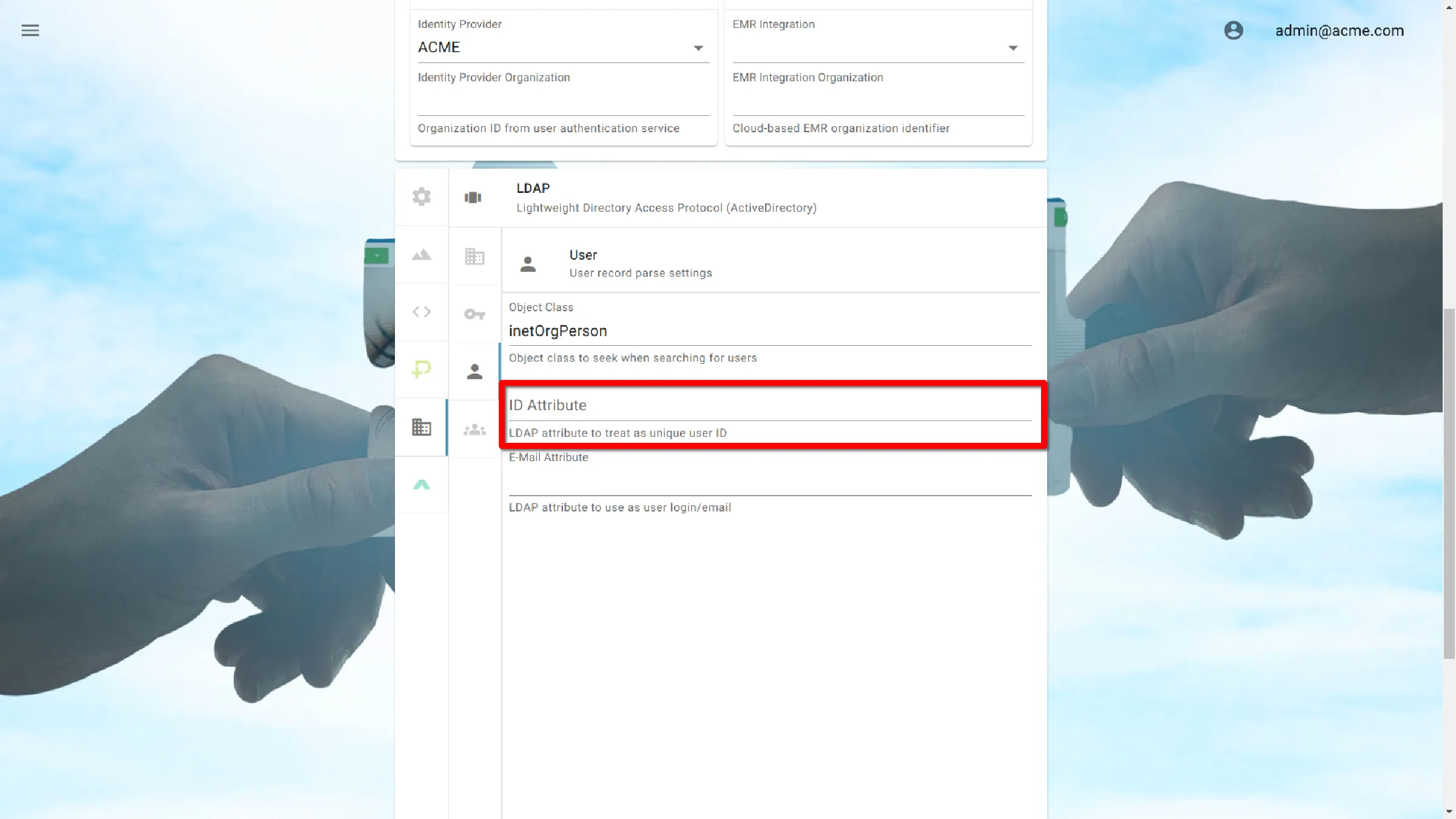
A unique attribute used to identify each user.
LDAP
uid
Active Directory
sAMAccountName
E-mail attribute
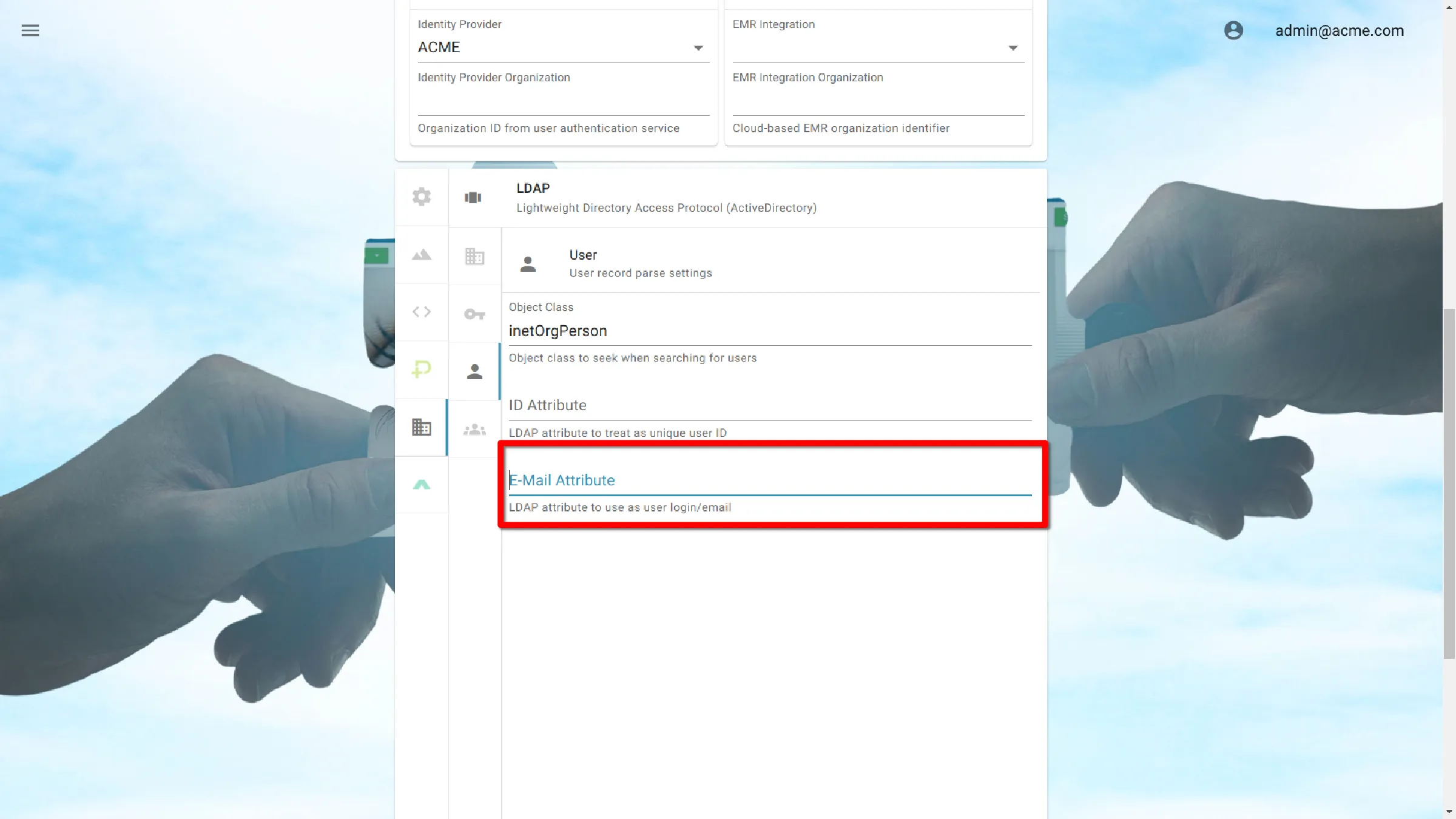
Attribute containing email address for user from server
LDAP
mail
Active Directory
userPrincipalName
Group Settings
Group Settings define attributes used to identify groups in the Directory Information Tree (DIT).
![]()
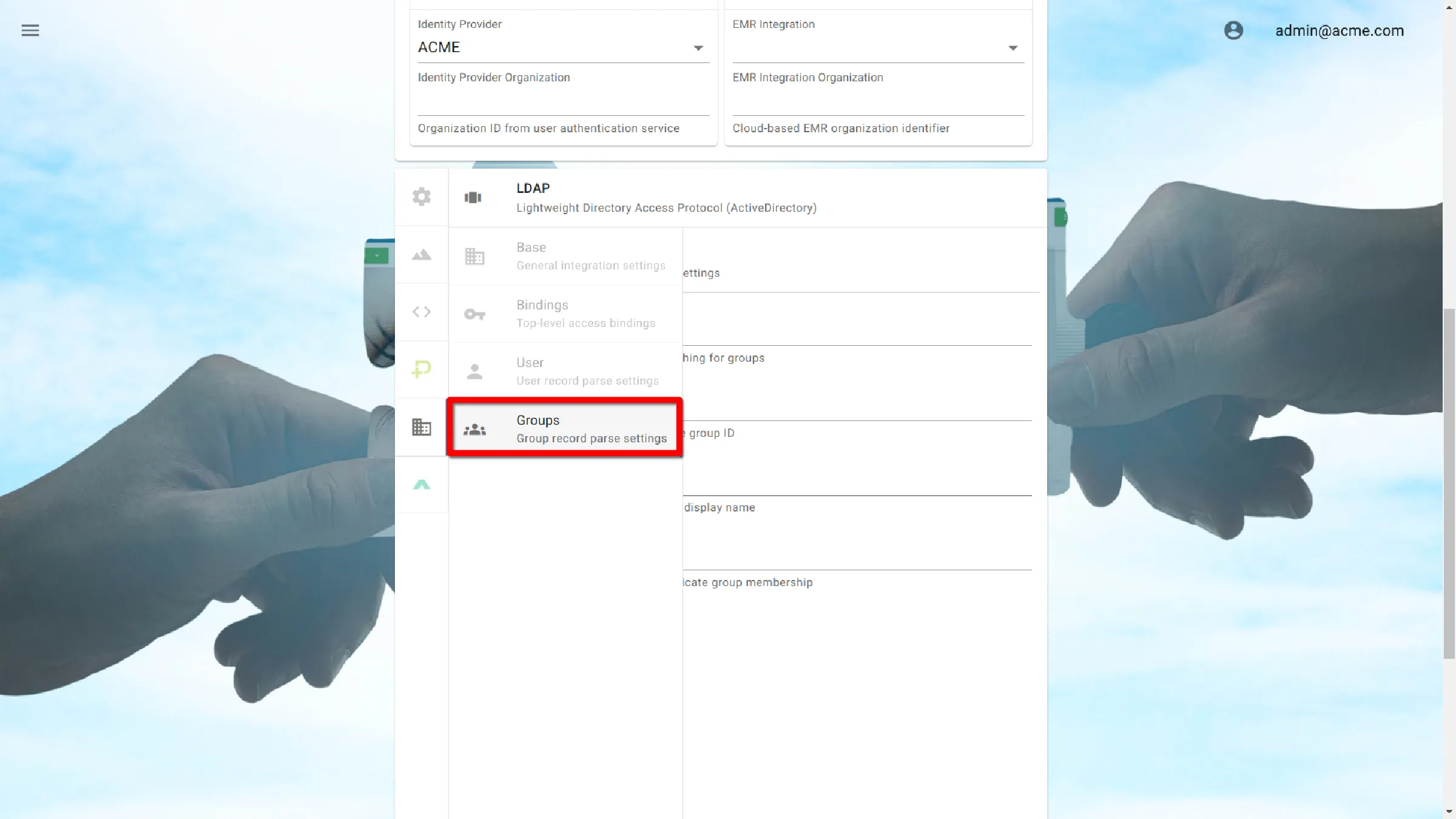
Object Class
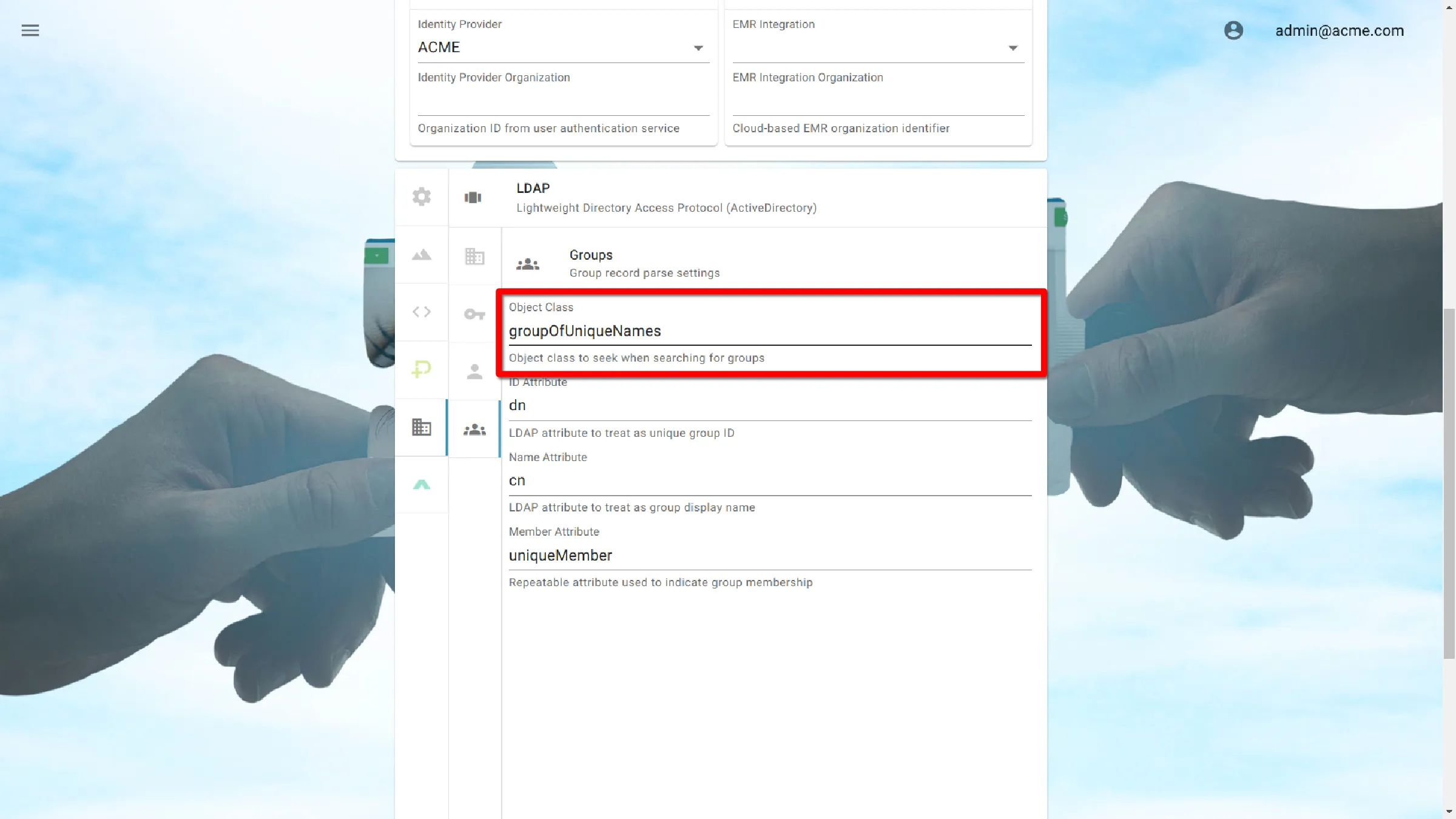
groupOfUniqueNames
ID Attribute
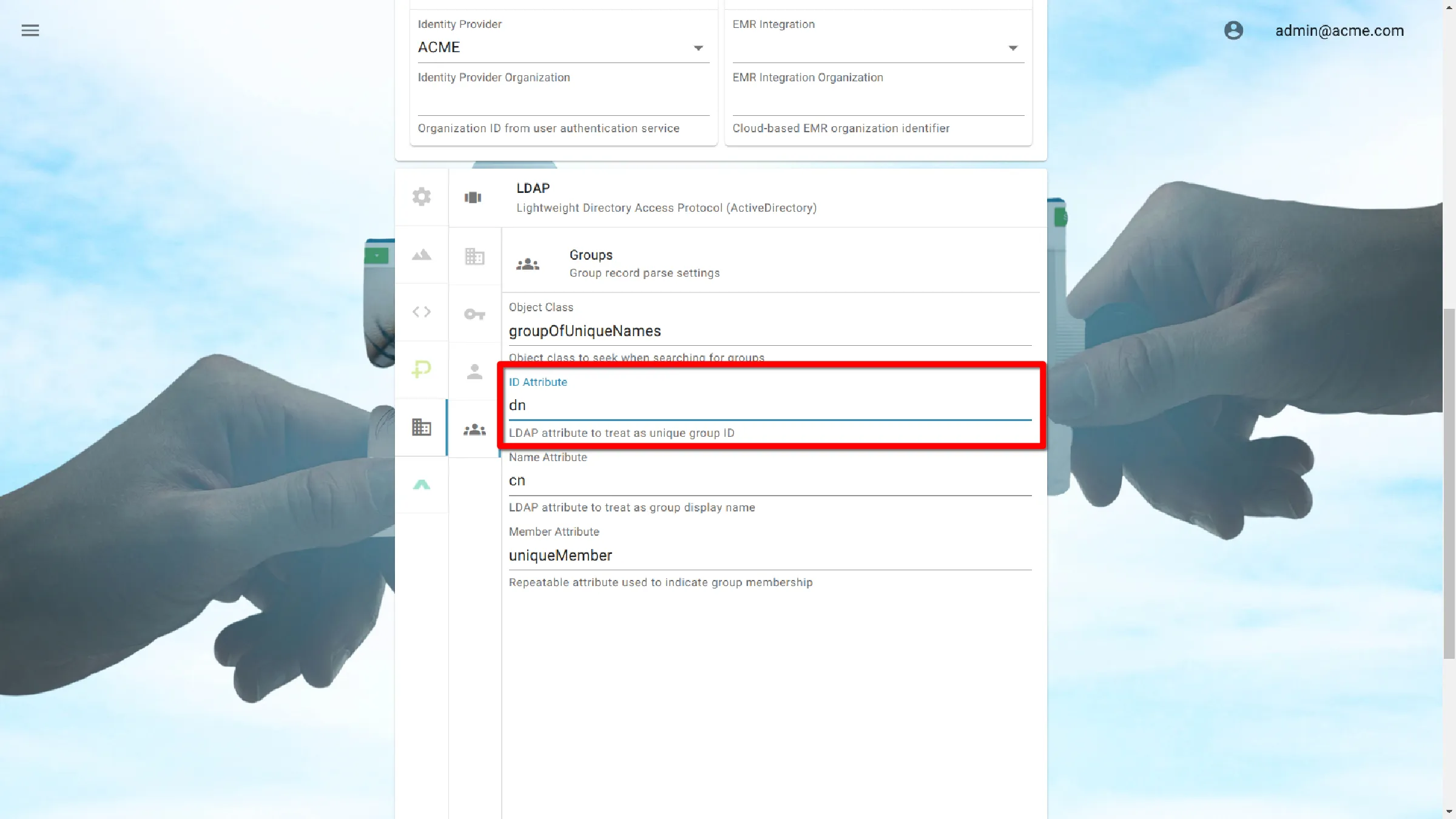
dn
Name Attribute
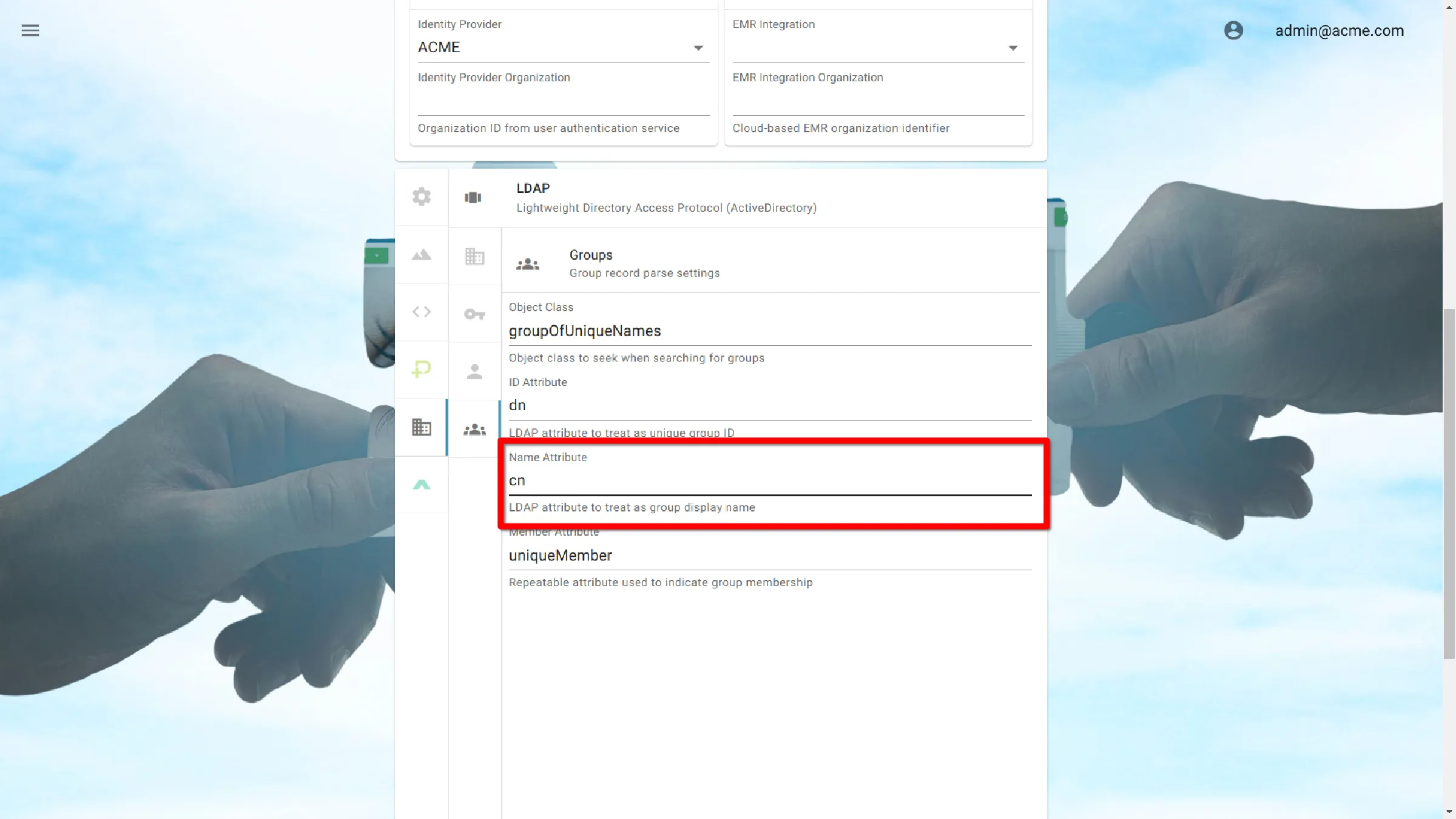
cn
Member Attribute
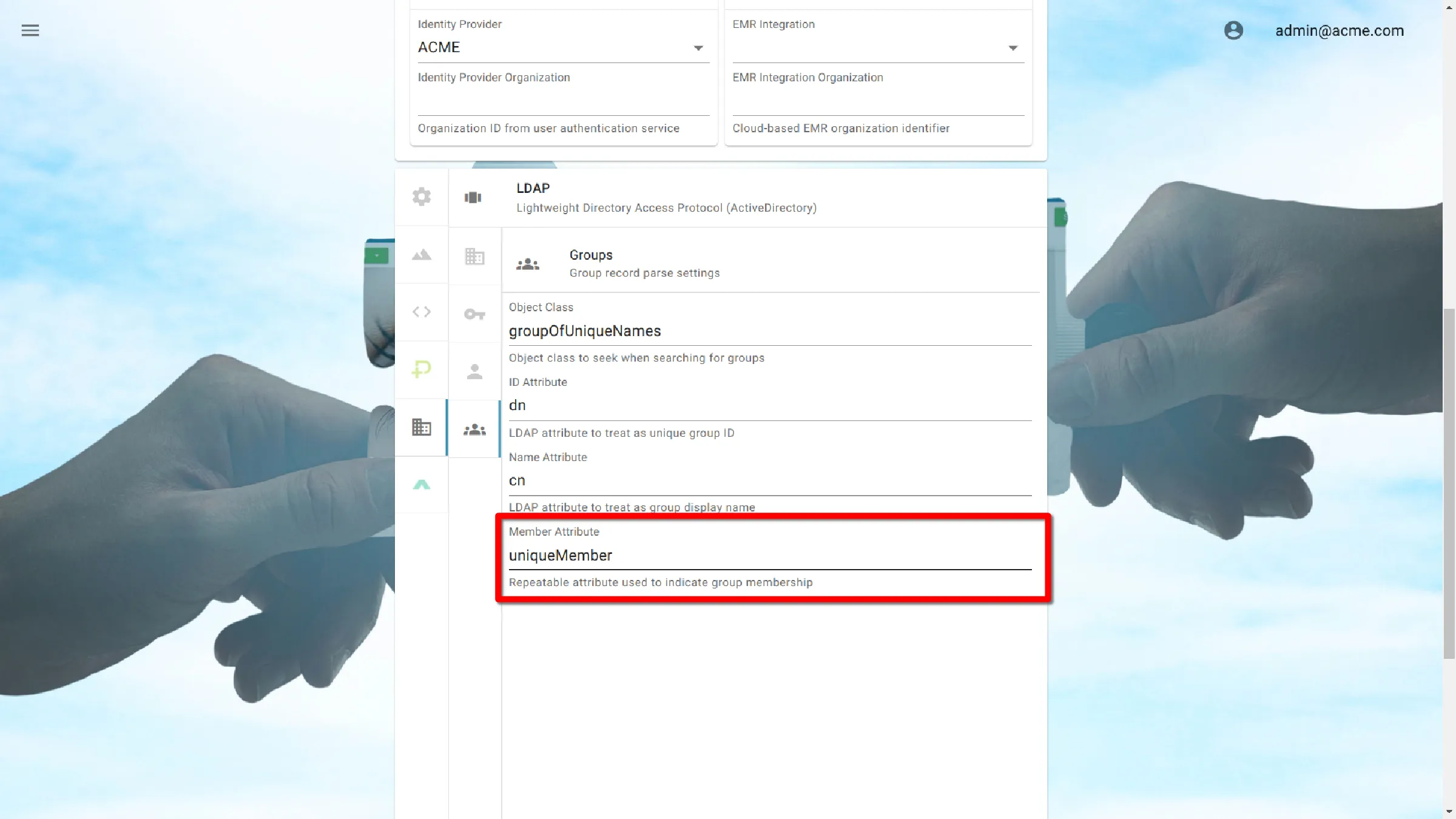
uniqueMember
Save Settings
Click the Submit button to save the settings.