OpenID Connect User Administration
The OpenID Connect integration allows users to authenticate to AGNES Connect using an existing OpenID Connect server, allowing users to take advantage of existing single sign on solutions. The OpenID Connect server must be publicly available on the internet to communicate with AGNES Connect servers. Each organization may connect to a single OpenID Connect server, replacing the user management module provided by AGNES Connect. These settings are typically configured by AMD employees during the initial deployment. Changing these settings may interfere with an organization’s ability to connect to AGNES. It’s recommended making changes to these settings under the guidance of AMD.
OpenID Connect Settings
The responsibility for OpenID Connect user management lies with the organization’s IT group. However, AMD recommends incorporating an administrative group called agnes_admin. When configured as the administrative group in AGNES, members of this group will gain administrative privileges in AGNES Connect.
Navigate to Organization Settings
Open Site Manager
To edit this setting, the logged-in user account must have an administrator role.
Right-click the AGNES Connect icon in the system tray and select Site Manager.
Select Organization from the navigation bar
Click the ’≡’ icon in the top left of the home screen, and select Organization from the navigation bar. If the option is not available, ensure the logged in user account has the administrator role.
Select OpenID Connect User Administration Settings
![]()
Issuer
: Hosted server identifier
Click the section labeled Issuer.
Issuer URI
URI for an OpenID Connect issuer.
Enter the Issuer URI
Client Credentials
: OpenID Connect client credentials
Click on the section labeled Client.
Prompt
OpenID Connect prompt parameter to pass with authorization requests.
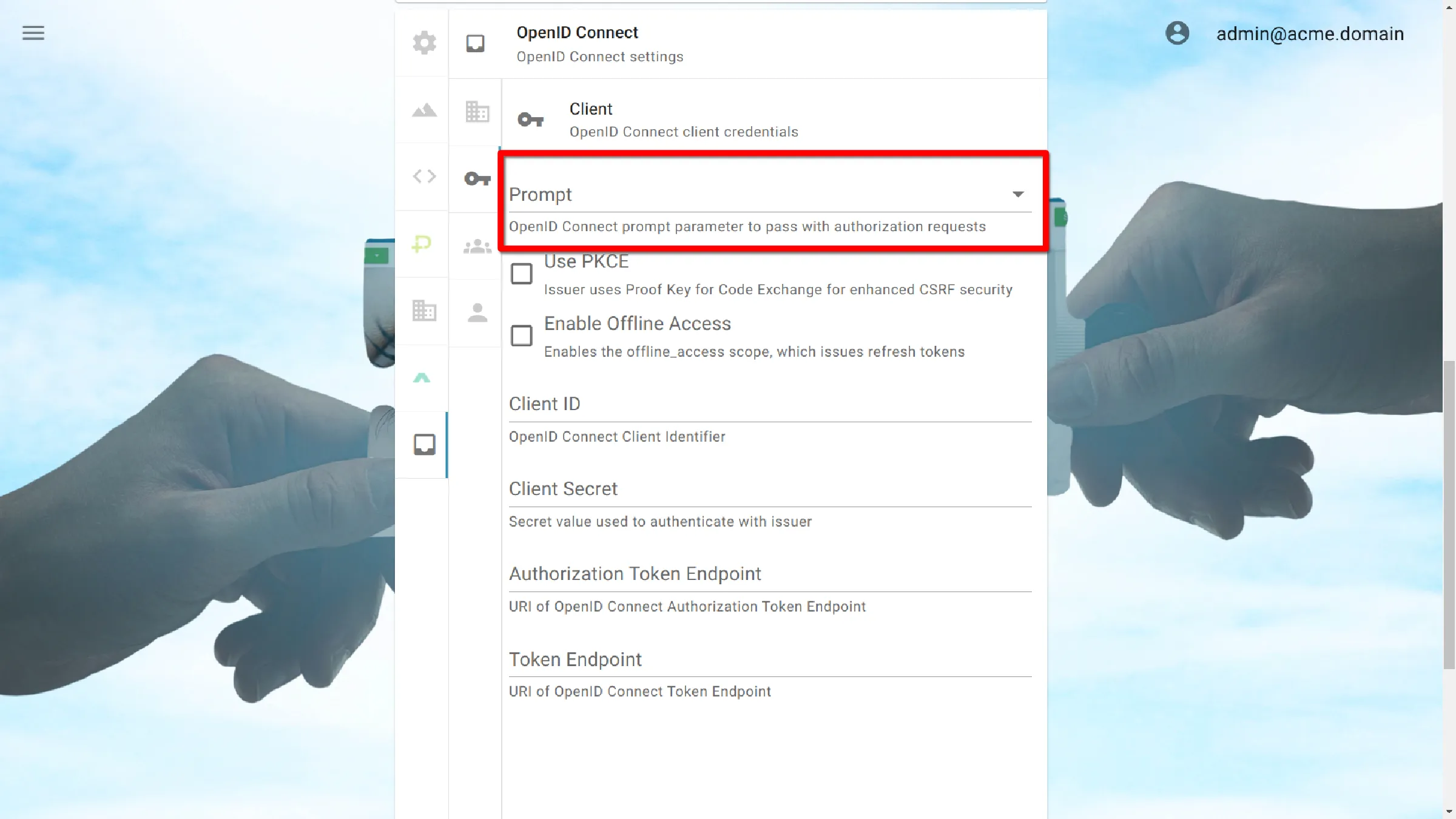
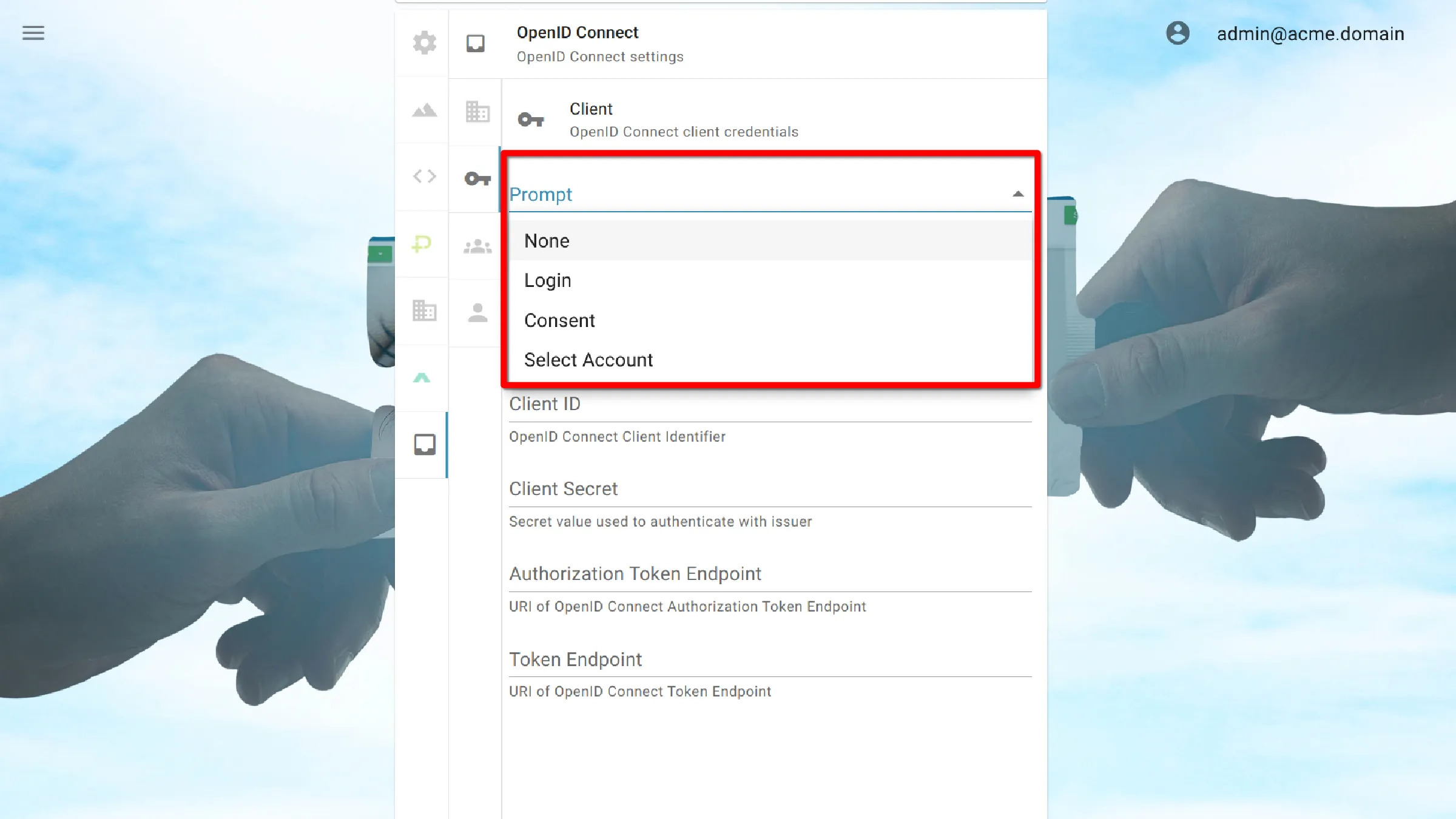
Click the dropdown labeled Prompt to show a list of options
- None: Attempt to bypass all interaction prompts
- Login: Require the user to re-enter their login credentials
- Consent: Request the user to approve any new or unapproved authorization scopes that have been requested
- Select Account: Ask the user to confirm which account to proceed with if there are multiple options
Use PKCE
Issuer uses Proof Key for Code Exchange for enhanced CSRF security.
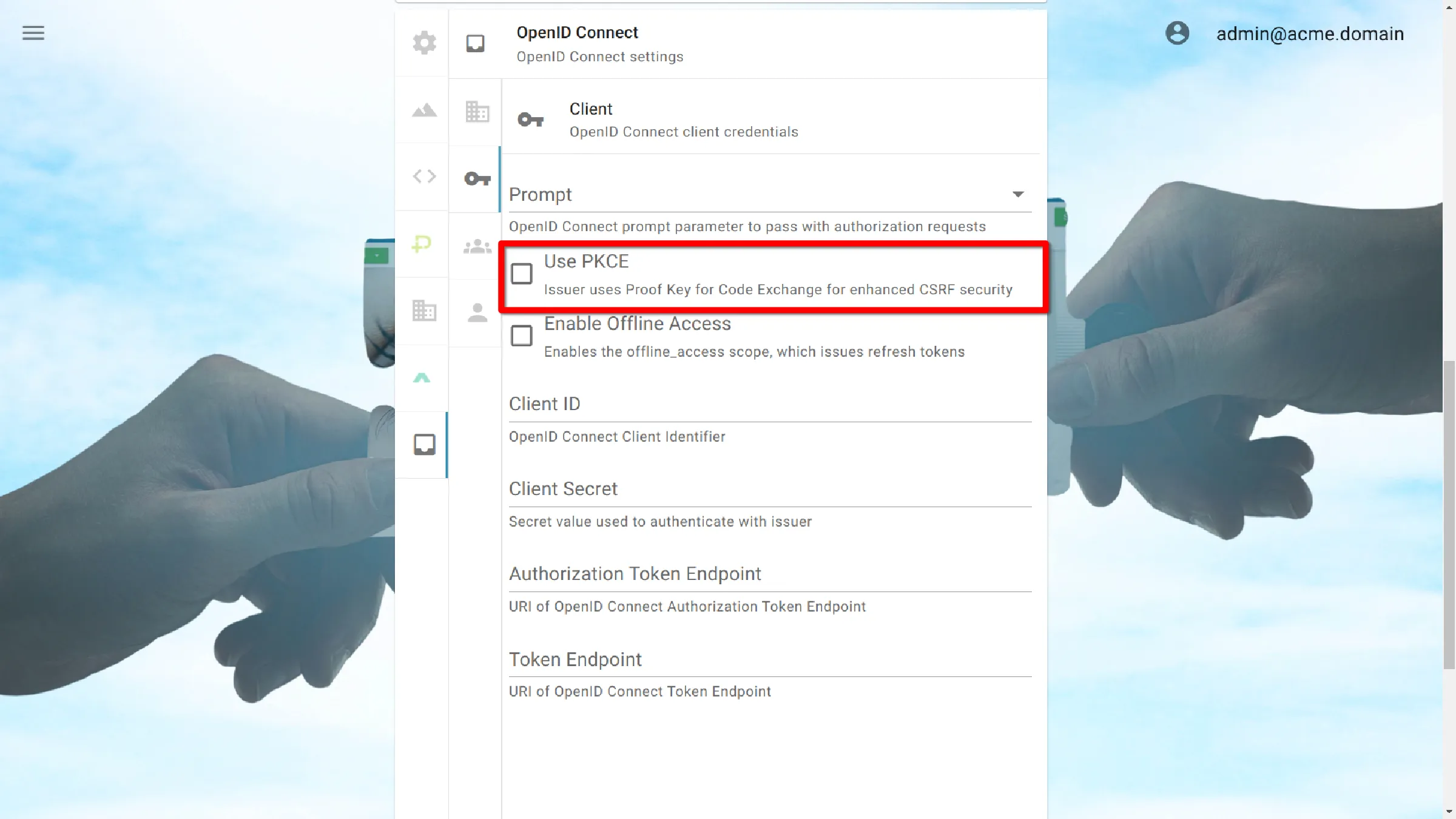
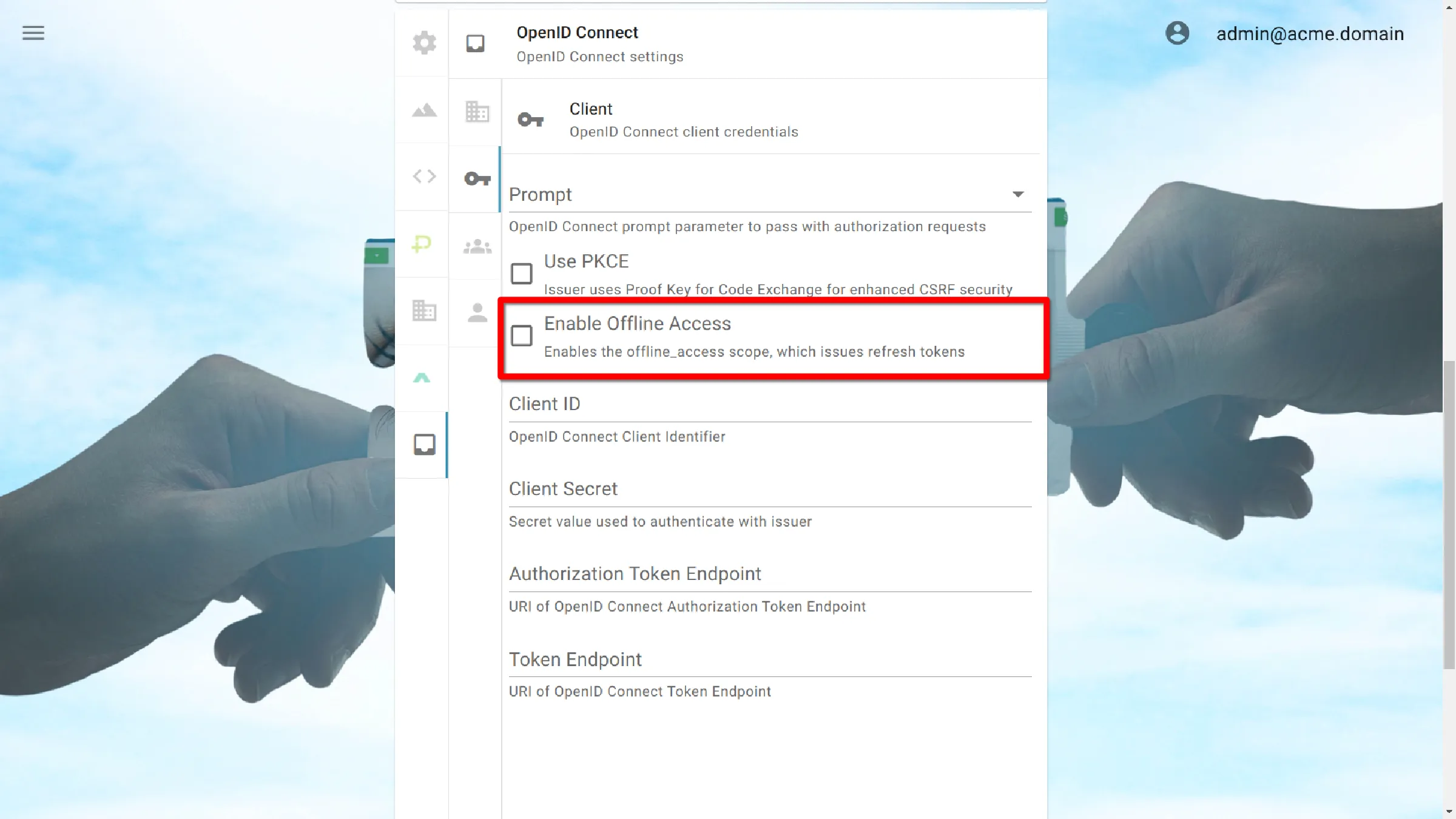
Enable Offline Access
Issuer uses Proof Key for Code Exchange for enhanced CSRF security.
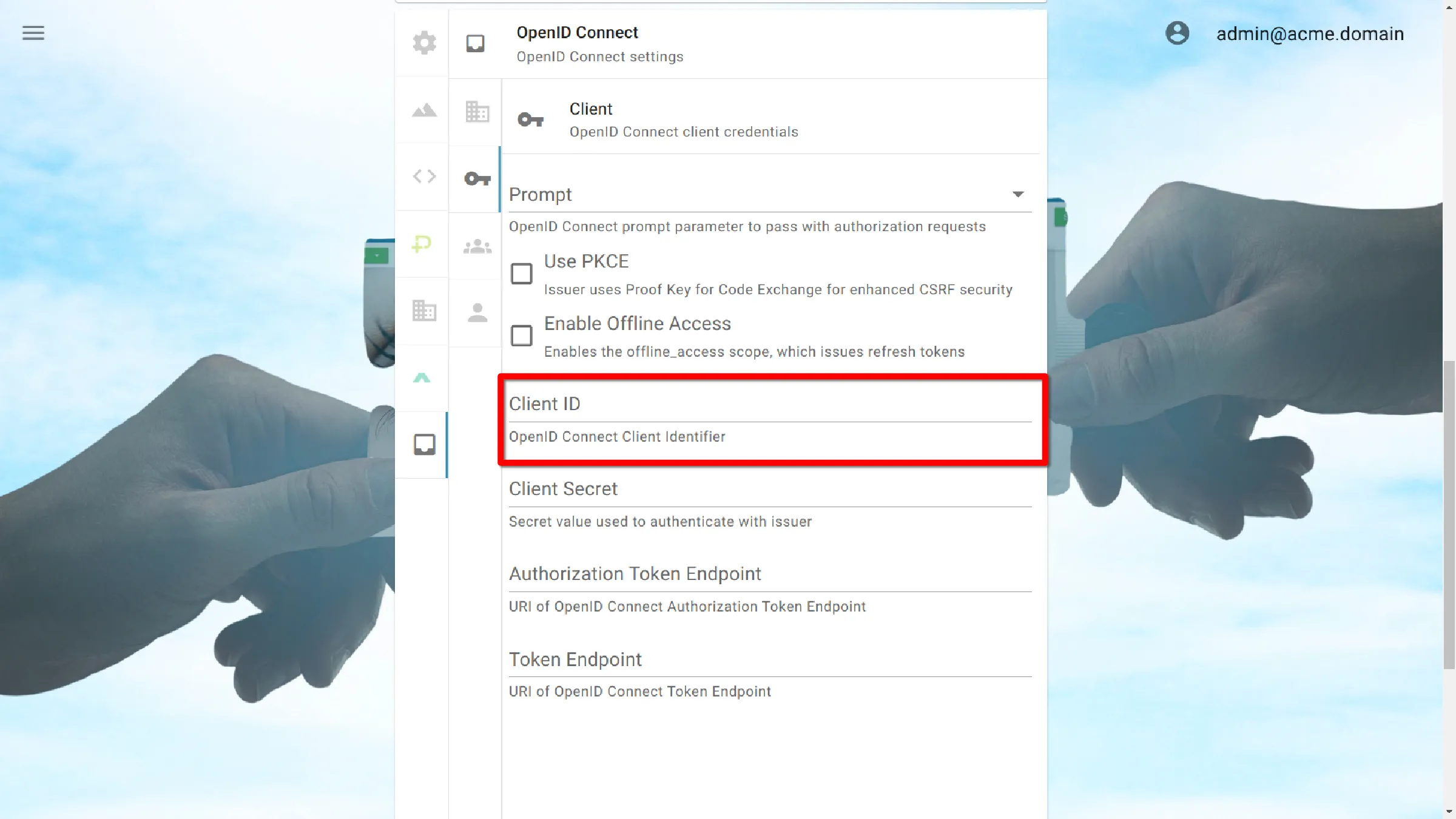
Client ID
OpenID Connect Client Identifier.
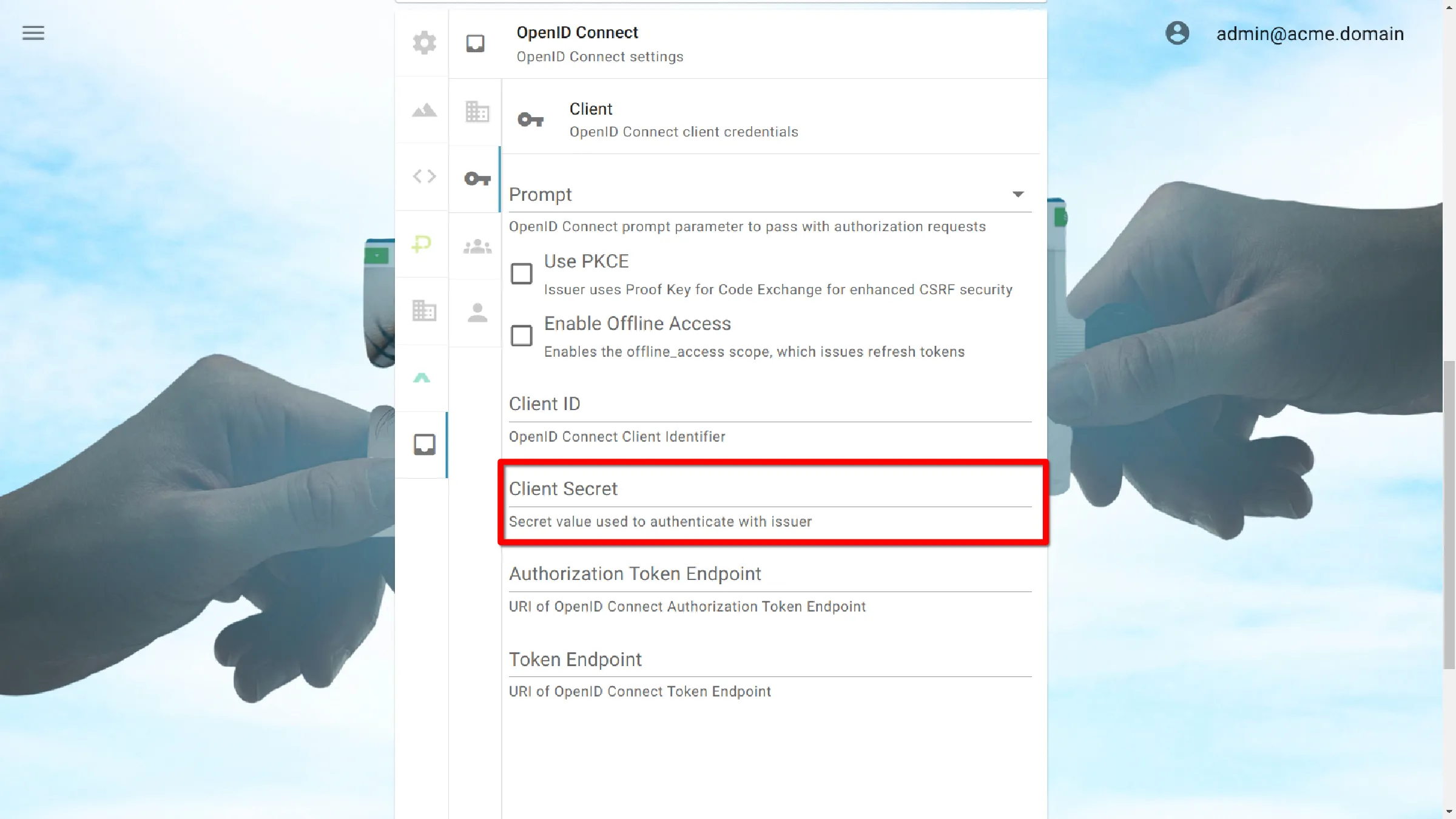
Client Secret
Secret value used to authenticate with issuer.
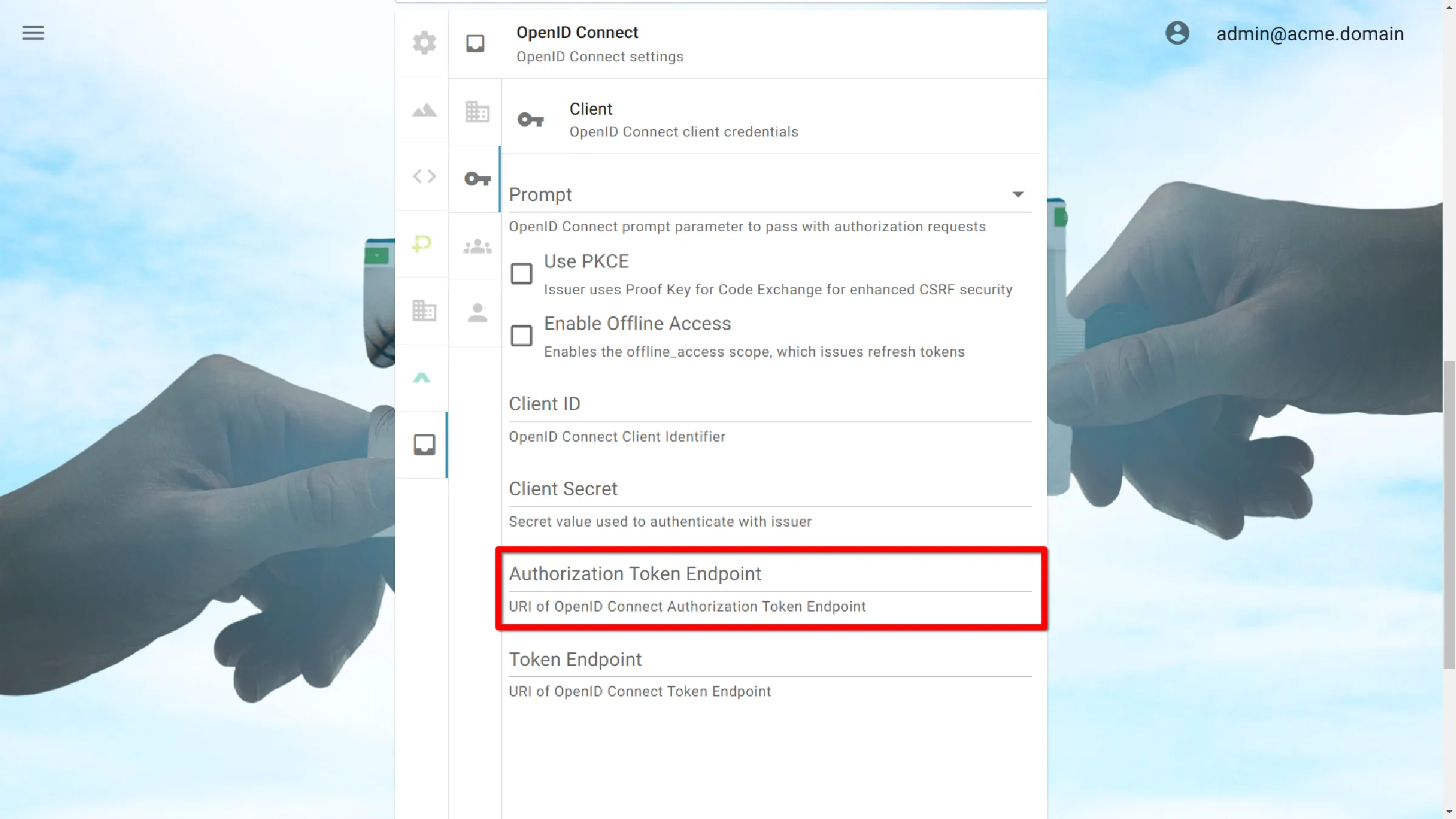
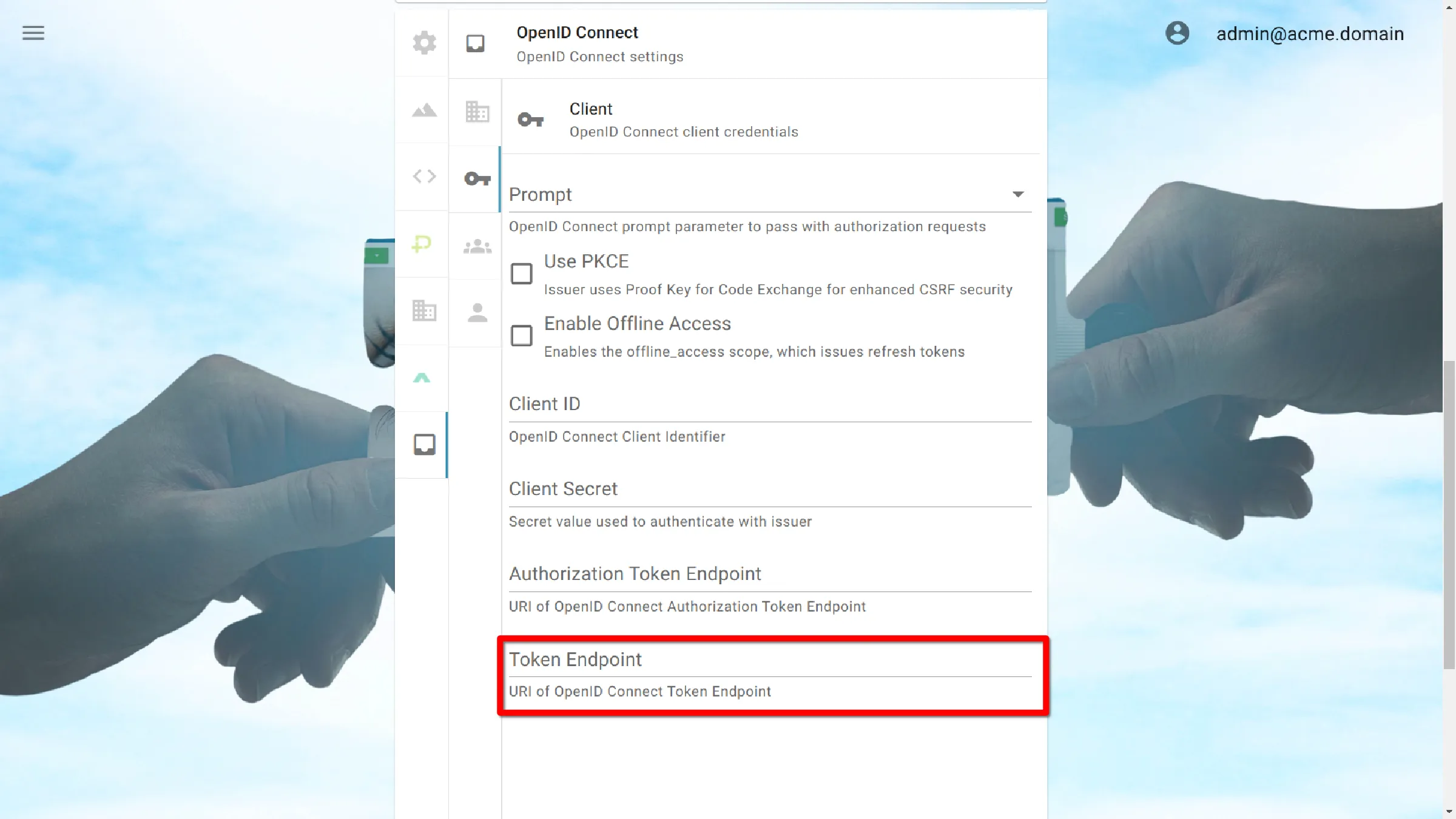
Authorization Token Endpoint
URI of OpenID Connect Authorization Token Endpoint.
Token Endpoint
URI of OpenID Connect Token Endpoint.
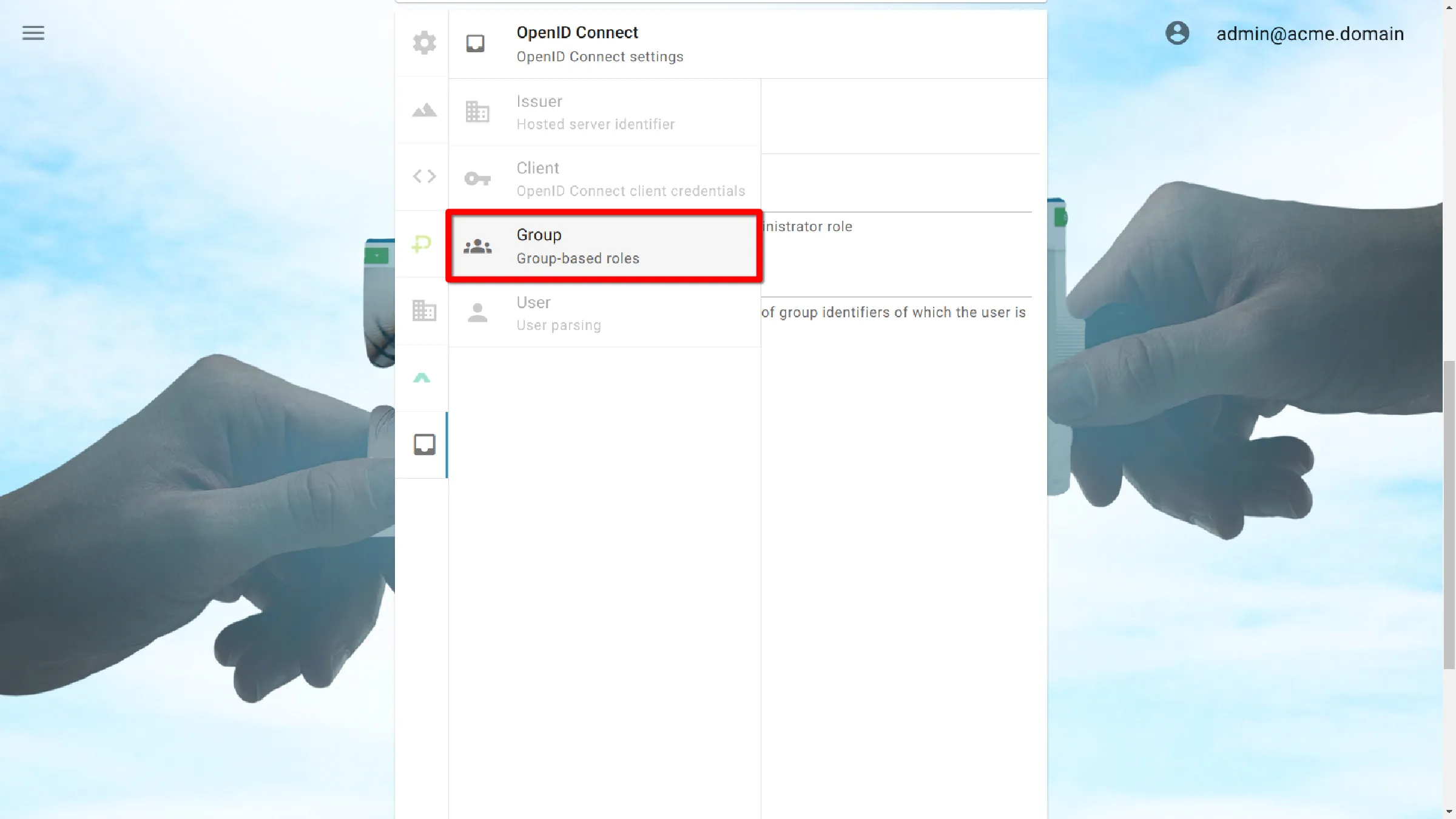
Group
: Group-based roles
Click on the section labeled Group.
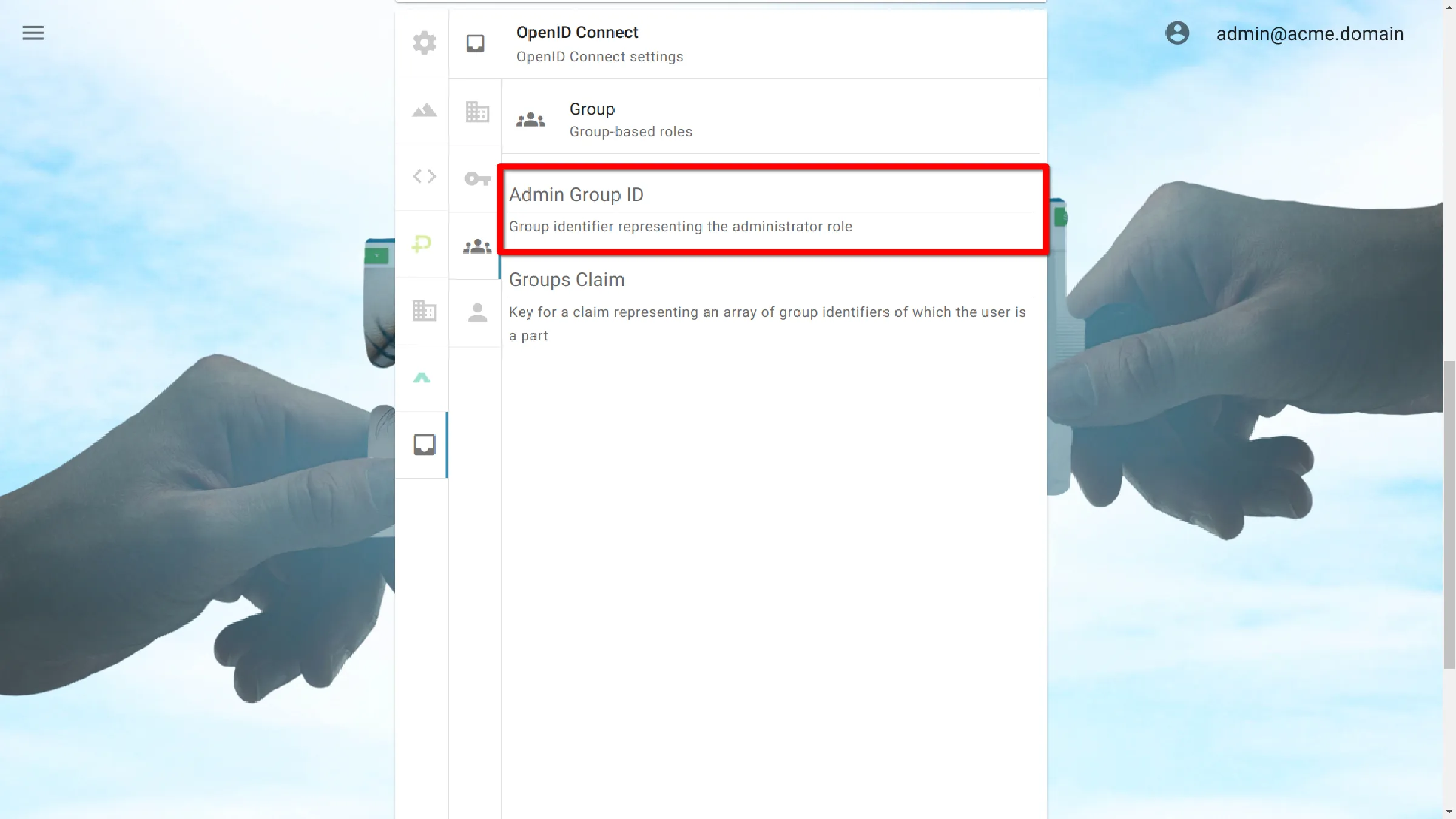
Admin Group ID
Group identifier representing the administrator role.
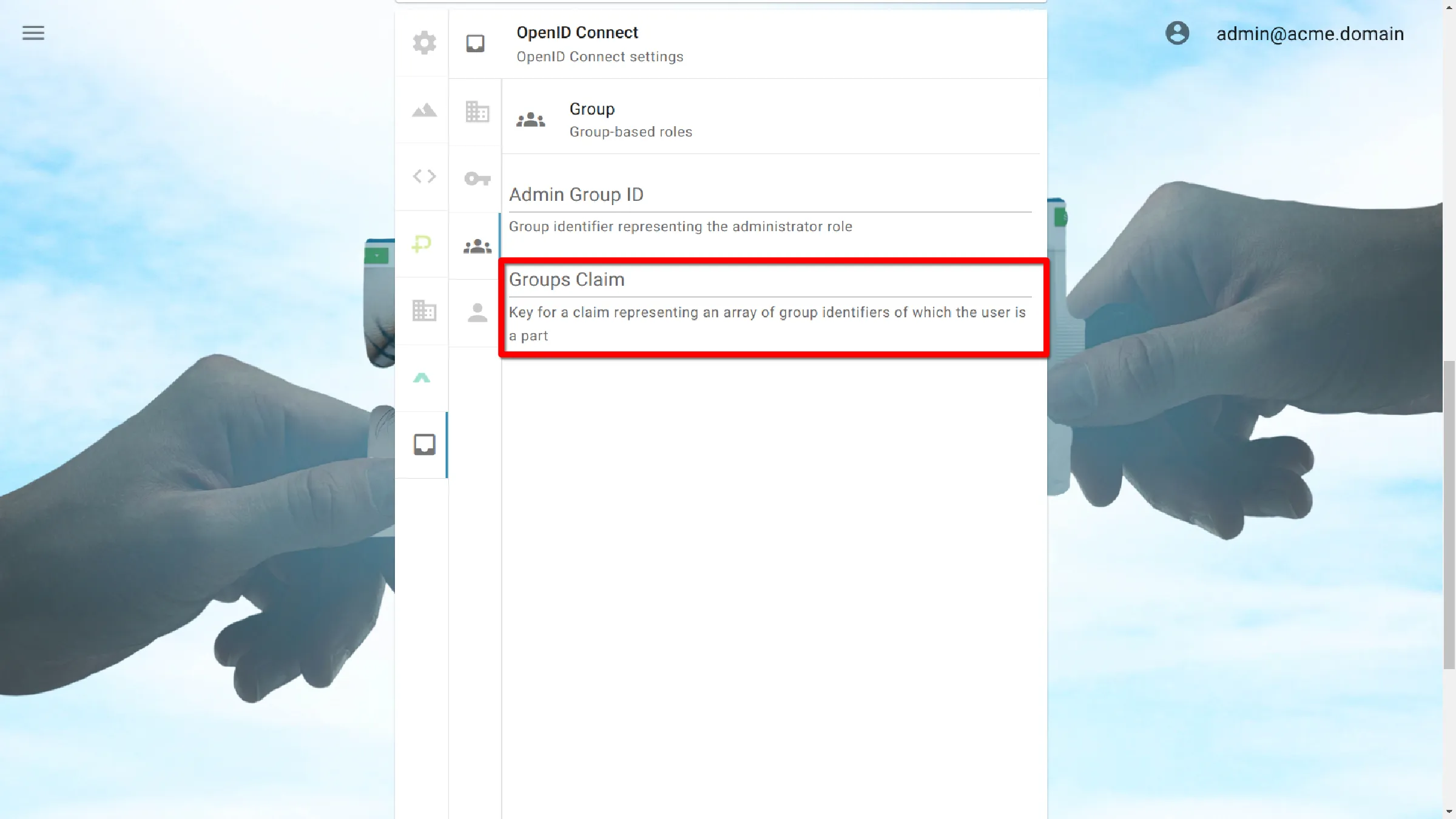
Groups Claim
Key for a claim representing an array of group identifiers of which the user is a part.
User Parsing
Provider Identifier Claim
Claim key to be used for identifying the user in EMR integrations.
Save Settings
Click the Submit button to save the settings.